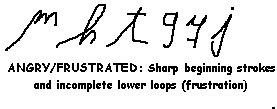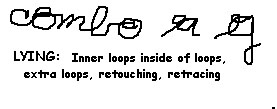NEPAL FORENSIC SOCIETY
Registered under the Nepal Law, Reg.No.622/053-54
|
|
JUSTICE BY FORENSIC SCIENCE
|
Courtesy: :MegaLinks in Criminal Justice, Internet QUESTIONED DOCUMENT EXAMINATION QUESTIONED
DOCUMENT A "questioned" document is any signature, handwriting, typewriting, or other mark whose source or authenticity is in dispute or doubtful. Letters, checks, driver licenses, contracts, wills, voter registrations, passports, petitions, threatening letters, suicide notes, and lottery tickets are the most common questioned documents, although marks on doors, walls, windows, or boards would also be included by definition.
Historically, QDE has been somewhat of an inclusive profession, even to the point where so-called pseudo-experts (in palmistry and fortune-telling) were sometimes welcome, and even today, it suffers from a bit of identity crisis in that at least eight (8) different, or related, areas can be identified:
It's probably a futile effort to rigidly demarcate and delimit the various areas of QDE as there will always be overlap, evolution, and, perhaps, controversy.
One of the things important to understand is what the QDE expert is looking for. This deals with the issue of class characteristics versus individual characteristics. In a nutshell, CLASS characteristics, which are commonly found at crime scenes, describe evidence which can only be associated with a group (like those with certain personality traits) and not a single source. Such evidence can only be used for corroboration or circumstantial purposes, and the evidentiary problem lies in the fact that little or no mathematical models exist to assess probability values with the comparison of class evidence. The expert must say things like "relatively certain" instead of things like "95% of the time" or "an odds-ratio of 300:1". INDIVIDUAL characteristics describe evidence that is associated with a common source and an extremely high level of probability. It's not so much that the evidence points directly at anything or anyone; it's that it draws an inevitable conclusion based on mathematical calculations or probabilities so high as to defy human comprehension while at the same time substantiated by the opinion of a scientific expert.
Among QDE experts, the use is made of many different scientific principles from a variety of disciplines, and one of the first attempts at basic principles appeared in Albert Osborn's Questioned Documents in 1910, grounded in handwriting comparison as evidence of individual characteristics (paraphrased below):
The psychological theory of handwriting comparison is developmental. Children learn to write by copying whatever style of writing is fashionable at the time and taught to them by teachers from textbooks. This style is known as the regular or national system, and for most of the twentieth century, it was either the Palmer system or the Zaner-Blosser system for cursive. Today, there are many systems, or no system. As the child grows, the act of writing becomes a subconscious effort and begins to pick up habitual shapes and patterns that distinguish it from all others. This is most evident with capital letters and numerals. Handwriting has individual characteristics due to it being largely unconscious behavior. The unconscious handwriting of two different individuals is never identical. Mechanical and physical factors, as well as the mental ones, make it highly unlikely that the exact same handwriting occurs in two different people. It's therefore important that samples, exemplars, or specimens (all synonymous terms for documents of known origin) be obtained under conditions as similar as possible to the conditions present at the time the disputed, doubtful, or original (all synonymous terms for questioned documents) was created. These conditions are an essential part of what are called standards of comparison:
Legally, the conditions in place that produced the specimen serve to authenticate it as a standard. Authentication, or positively establishing the origin of known documents, is required for any piece of documentary evidence. This can be accomplished by the testimony of witnesses who saw the original writing produced, by the testimony of persons familiar with the writing, or (in some states) by a post litem motam courtroom demonstration where the writer gives a sample which is checked within an hour to a day or more by a QDE expert. Technically, even the police could extract authenticated samples since neither Fourth nor Fifth Amendment rights apply to handwriting samples. In addition, some samples are self-authenticating -- as in any writing on legal forms, business correspondence, responses to communication from others, and some "ancient" documents (over 30 years old). Irregularities in the authentication (or discovery) process of a handwriting case are NOT grounds for reversible error. The accused may get a new trial, but they are not exculpated or found innocent by most courtroom errors. Refusal by the accused to give a handwriting sample is presumptive evidence of guilt. There's no right to remain silent when it comes to handwriting. A potential problem exists with signatures. People usually have three (3) different signatures: (1) a formal one, used on important documents; (2) a routine one, used on regular correspondence; and (3) an informal one, used for jotting quick notes. Also, other circumstances affect writing such as age, arthritis, emotional distress, medication, intoxication, and corrective vision. It's difficult to tell handedness, gender, and age from unknown samples. QDE experts must consider all these things, and make an informed judgement (usually in consultation with an investigator or attorney) based on their familiarity with handwriting dynamics (e.g., appearance, laborious movements, rhythm). With an impairment like arthritis, for example, the writing function may become more of a conscious than subconscious effort, making for a more complex case. However, a paraphrasing of Larry Miller's (1987) indicia drawn from a review of the forgery literature might provide useful guidelines when dealing with impaired or deliberately deceptive writing:
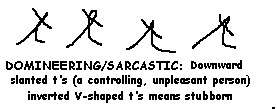
Problems get stickier when trying to draw personality inferences from handwriting samples. Remember this is the realm of graphology, but it might be interesting to look at a few traits of interest to criminal justice and criminology. With that in mind, here's a small, academic fair use sample of the Trait Dictionary from Bart Bagget's MyHandwriting.com. Be advised that these are not definitive interpretations by any means because there are over 30 different "systems" of graphology in existence.
Graphology systems tend to be one of three (3) types: (1) those based on individual letter formations; (2) those based on stroke analysis; and (3) those based on an holistic/gestalt method. Over 3000 private business companies use it routinely (to screen employees), and it enjoys a growing sense of scientific respectability. The courts appear to be waiting to see college psychology courses on it. It probably has the most validity with the following domains: (1) intelligence; (2) attitude toward work; and (3) interpersonal skills. Recent developments have focused on "profiling" of uncaptured criminals and sex offenders (where handwriting analysts say they can spot a "perversion", not exactly the best word for it). There's some precedent in art therapy and projective psychological testing for graphology. Many convictions of child sex offenders have occurred because of what the child victim portrayed in a drawing, and with psychological testing, there's the famous "Draw a Pig" assignment, which apparently contains everything you need to make a subjective personality assessment from: where placed on paper; the size of the pig; the pressure applied; the direction the pig is facing; attention to details; line quality; angular or curved strokes; and emphasis on head of pig. GO TO TOP
Court-recognized expertise as a QDE expert is not something that can be achieved through self-study alone. An old common law rule that isn't recognized much anymore says that one can become an expert by study without practice or by practice without study. With QDE, the courts (State v. Evans 1991) have decided that a person needs both: study and practice -- that is, a period of training (internshiip or apprenticeship is better than a self-study course) and a period of experience (twenty some previous cases worked on is a good average). In addition, there's a rather large literature base to become familiar with, and a good number of journals, periodicals and newsletters.
Computer forensics is used in many areas. In civil law for discrimination and harassment cases, by insurance companies for workman's compensation cases, by corporations for trade secret misappropriations, and in criminal law mostly for drug and embezzlement record-keeping and child pornography. As mentioned previously, this is a loosely related, developing specialty area. It is most closely related to typewriting comparison. The FBI has, for many years, maintained typewriter databases, ink databases, copy toner databases, paper databases, and watermarks (which sometimes change every year). Private examiners do not have the advantage of large databases available to government examiners. Computers and computer printouts also leave a trail that can be followed, whether it's from something simple like how full or dry a printer ink cartridge is, to the various alignments and misalignments of dot matrix and laser printers, to fiber analysis of the paper used, computer crime specialists utilize some of the same age-old techniques that typewriting analysts used as well as other investigative methods. A computer forensics expert will have experience on a wide variety of hardware and software. Unlike paper evidence, computer evidence exists in many forms, with earlier, alternate, and backup versions of each and every file somewhere on the hard drive and frequently unknown to the user. The process of examining a suspect computer system is as follows:
|
|
|