Biometrics
-Information Compiled by Abhijith HN
ProZone : Articles : Biometrics
Index
1. Introduction
3. What biological measurements qualify to be a biometric?
4. Biometric system - How it works?
8. Advantages & Disadvantages of biometrics.
10. Summary.
11. Glossary
1. Introduction
A wide variety of systems require reliable personal recognition schemes to either confirm or determine the identity of an individual requesting their services. The purpose of such schemes is to ensure that the rendered services are accessed only by a legitimate user, and not anyone else. Biometric recognition, or simply biometrics, refers to the automatic recognition of individuals based on their physiological and/or behavioral characteristics. By using biometrics it is possible to confirm or establish an individual’s identity based on “who she is”, rather than by “what she possesses” (e.g., an ID card) or “what she remembers” (e.g., a password).
BIOMETRICS is the measurement of biological data. The term Biometrics is derived from a Greek word and means “life measure”. The term biometrics is commonly used today to refer to the authentication of a person by analyzing physiological characteristics, such as fingerprints, or behavioral characteristics, such as signatures. Since many physical and behavioral characteristics are unique to an individual, biometrics provides a more reliable system of authentication than ID cards, keys, Passwords or other traditional systems.
Physiological traits are stable physical characteristics, such as palm prints and iris patterns. This type of measurement is essentially unalterable. A Behavioral characteristic — such as one's signature, voice, or keystroke dynamics — is influenced by both controllable actions and less controllable psychological factors. Because behavioral characteristics can change over time, the enrolled biometric reference template must be updated each time it is used. Although behavior-based biometrics can be less expensive and less threatening to users, physiological traits tend to offer greater accuracy and security. In any case, both techniques provide a significantly higher level of identification than passwords or smart cards alone.
Because biometric traits are unique to each individual, they can be used to prevent theft or fraud. Unlike a password or personal identification number (PIN), a biometric trait cannot be forgotten, lost, or stolen. Today there are over 10,000 computer rooms, vaults, research labs, day care centers, blood banks, ATMs and military installations to which access is controlled using devices that scan an individual's unique physiological or behavioral characteristics.
2. Definition of Biometrics
Biometrics, strictly speaking, refers to a science involving the statistical analysis of biological characteristics. Today, the term "biometrics" usually refers to technologies that analyze human characteristics for security purposes. The statistical science of biometrics continues in the background and should be treated separately. A de facto definition of security-based biometrics has been circulating for a number of years:
A biometric is a unique, measurable characteristic or trait of a human being for automatically recognizing or verifying identity.
Biometric technologies, therefore, are concerned with the physical parts of the human body or the personal traits of human beings.
3. What biological measurements qualify to be a biometric?
Any human physiological and/or behavioral characteristic can be used as a biometric characteristic as long as it satisfies the following requirements:
· Universality: each person should have the characteristic;
· Distinctiveness: any two persons should be sufficiently different in terms of the
characteristic;
· Permanence: the characteristic should be sufficiently invariant (with respect to the matching criterion) over a period of time;
· Collectability: the characteristic can be measured quantitatively.
However, in a practical biometric system (i.e., a system that employs biometrics for personal recognition), there are a number of other issues that should be considered, including:
· Performance, which refers to the achievable recognition accuracy and speed, the resources required to achieve the desired recognition accuracy and speed, as well as the operational and environmental factors that affect the accuracy and speed;
· Acceptability, which indicates the extent to which people are willing to accept the use of a particular biometric identifier (characteristic) in their daily lives;
· Circumvention, which reflects how easily the system can be fooled using fraudulent methods.
A practical biometric system should meet the specified recognition accuracy, speed, and resource requirements, be harmless to the users, be accepted by the intended population, and be sufficiently robust to various fraudulent methods and attacks to the system.
4. Biometric Systems – How it works?
First, the system captures a sample of the biometric characteristic (this is known as the enrollment process). During enrollment, some biometric systems may require a number of samples in order to build a profile of the biometric characteristic. Unique features are then extracted and converted by the system into a mathematical code. This sample is then stored as the biometric template for the enrollee. The template may reside in the biometric system itself, or in any other form of memory storage, such as a computer database, smart card or barcode.
In addition, the biometric system may require a trigger, or a means of tying the template to the person. For example, a personal identification number (PIN) is keyed in to access the template, or a smart card storing the template is inserted into a card reader. In either case, the end user interacts with the biometric system a second time to have his or her identity checked. A new biometric sample is taken and this is compared to the template. If the template and the new sample match, the end user is granted access. This is the basic premise of biometrics — that a person has a sample of their biometric data captured and the biometric system decides if it matches with another sample.
Because both physical and behavioral characteristics can change slightly over time (e.g., a finger can be scarred and a signature may change as a person gets older), the biometric system must allow for these subtle changes, so a threshold is set. This can take the form of an accuracy score. In this case, comparison between the template and new sample must exceed the system's threshold before a match is recorded. In other words, if the new biometric sample is sufficiently similar to the previously stored template, the system will determine that the two do in fact match. If not, the system will not record a match and will not identify the end user. This use of a threshold gives biometric technologies a significant advantage over passwords, PIN’s and ID badges. With biometrics, it doesn't matter if you forget your password or lose your ID. The use of a threshold affords a tremendous degree of flexibility and if the comparison between the new biometric sample and the template exceeds the stated threshold, identity will be confirmed.
All biometric systems use the four-stage process of capture, extraction, comparison, and match, but employ different methods and techniques to deal with the human factor (stress, general health, working and environmental conditions, and time pressures all conspire to make humans inconsistent). At the heart of the biometric system is the biometric engine, a proprietary element that extracts and processes the biometric data. This may apply an algorithm or an artificial neural network. It extracts the data, creates a template, and computes whether the data from the template and the new sample match.
The following four-stage process illustrates the way biometric systems operate:
- Capture — a physical or behavioral sample is captured by the system during enrollment.
- Extraction — unique data is extracted from the sample and a template is created.
- Comparison or Matcher— the template is then compared with a new sample.
- Match/Non-Match — the system then decides if the features extracted from the new sample are a match or a non-match.
A biometric system is essentially a pattern recognition system that operates by acquiring biometric data from an individual, extracting a feature set from the acquired data, and comparing this feature set against the template set in the database. Depending on the application context, a biometric system may operate either in verification mode or identification mode:
Verification Mode: In the verification mode, the system validates a person’s identity by comparing the captured biometric data with her own biometric template(s) stored system database. In such a system, an individual who desires to be recognized claims an identity, usually via a PIN (Personal Identification Number), a user name, a smart card, etc., and the system conducts a one-to one comparison to determine whether the claim is true or not (e.g., “Does this biometric data belong to Bob?”). Identity verification is typically used for positive recognition, where the aim is to prevent multiple people from using the same identity.
Identification Mode: In the identification mode, the system recognizes an individual by searching the templates of all the users in the database for a match. Therefore, the system conducts a one-to-many comparison to establish an individual’s identity (or fails if the subject is not enrolled in the system database) without the subject having to claim an identity (e.g., “Whose biometric data is this?”). Identification is a critical component in negative recognition applications where the system establishes whether the person is who she (implicitly or explicitly) denies to be. The purpose of negative recognition is to prevent a single person from using multiple identities. Identification may also be used in positive recognition for convenience (the user is not required to claim an identity). While traditional methods of personal recognition such as passwords, PINs, keys, and tokens may work for positive recognition, negative recognition can only be established through biometrics.
The same four-stage process — capture, extraction, comparison, and match/non-match — applies equally to identification, recognition and verification.
The block diagrams of a verification system and an identification system are depicted in Figure 1; user enrollment, which is common to both the tasks is also graphically illustrated.

Figure 1. Block diagrams of enrollment, verification and identification tasks are shown using the four main modules of a biometric system, i.e., sensor, feature extraction, matcher, and system database.
A biometric system is designed using the following four main modules (see Figure 1):
1. Sensor module, which captures the biometric data of an individual. An example is a
fingerprint sensor that images the ridge and valley structure of a user’s finger.
2. Feature extraction module, in which the acquired biometric data is processed to extract a set of salient or discriminatory features. For example, the position and orientation of minutiae points (local ridge and valley singularities) in a fingerprint image are extracted in the feature extraction module of a fingerprint-based biometric system.
3. Matcher module or comparison, in which the features during recognition are compared against the stored templates to generate matching scores. For example, in the matching module of a fingerprint-based biometric system, the number of matching minutiae between the input and the template fingerprint images is determined and a matching score is reported. The matcher module also encapsulates a decision making module, in which a user's claimed identity is confirmed (verification) or a user’s identity is established (identification) based on the matching score.
4. System database module, which is used by the biometric system to store the biometric templates of the enrolled users. The enrollment module is responsible for enrolling individuals into the biometric system database. During the enrollment phase, the biometric characteristic of an individual is first scanned by a biometric reader to produce a digital representation (feature values) of the characteristic. The data capture during the enrollment process may or may not be supervised by a human depending on the application. A quality check is generally performed to ensure that the acquired sample can be reliably processed by successive stages. In order to facilitate matching, the input digital representation is further processed by a feature extractor to generate a compact but expressive representation, called a template. Depending on the application, the template may be stored in the central database of the biometric system or be recorded on a smart card issued to the individual. Usually, multiple templates of an individual are stored to account for variations observed in the biometric trait and the templates in the database may be updated over time.
5. Biometric errors
Two samples of the same biometric characteristic from the same person (e.g., two impressions of a user’s right index finger) are not exactly the same due to imperfect imaging conditions (e.g., sensor noise and dry fingers), changes in the user’s physiological or behavioral characteristics (e.g., cuts and bruises on the finger), ambient conditions (e.g., temperature and humidity) and user’s interaction with the sensor (e.g., finger placement).
A biometric verification system makes two types of errors: (1) mistaking biometric
measurements from two different persons to be from the same person (called false match), and (2) mistaking two biometric measurements from the same person to be from two different persons (called false non-match). These two types of errors are often termed as false accept and false reject, respectively.
6. Types of Biometrics
DNA: Deoxyribo Nucleic Acid (DNA) is the one-dimensional ultimate unique code for one’s individuality - except for the fact that identical twins have identical DNA patterns. It is, however, currently used mostly in the context of forensic applications for person recognition. Three issues limit the utility of this biometrics for other applications: (i) contamination and sensitivity: it is easy to steal a piece of DNA from an unsuspecting subject that can be subsequently abused for an ulterior purpose; (ii) automatic real-time recognition issues: the present technology for DNA matching requires cumbersome chemical methods (wet processes) involving an expert’s skills and is not geared for on-line non-invasive recognition; (iii) privacy issues: information about susceptibilities of a person to certain diseases could be gained from the DNA pattern and there is a concern that the unintended abuse of genetic code information may result in discrimination, e.g., in hiring practices.
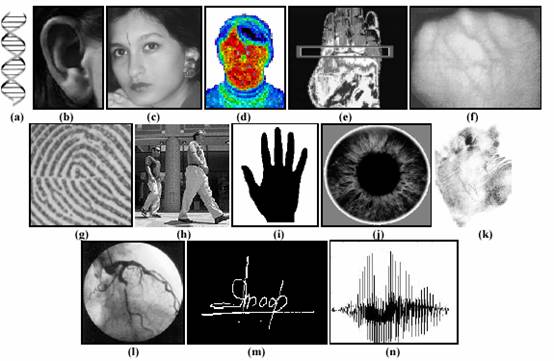
Figure 2. Examples of biometric characteristics: a) DNA, b) ear, c) face, d) facial thermogram, e) hand thermogram, f) hand vein, g) fingerprint, h) gait, i) hand geometry, j) iris, k) palmprint, l) retina, m) signature, and n) voice.
Ear: It has been suggested that the shape of the ear and the structure of the cartilaginous tissue of the pinna are distinctive. The ear recognition approaches are based on matching the distance of salient points on the pinna from a landmark location on the ear. The features of an ear are not expected to be very distinctive in establishing the identity of an individual.
Face: Face recognition is a non-intrusive method, and facial images are probably the most common biometric characteristic used by humans to make a personal recognition. The applications of facial recognition range from a static, controlled “mug-shot” verification to a dynamic, uncontrolled face identification in a cluttered background (e.g., airport). The most popular approaches to face recognition are based on either (i) the location and shape of facial attributes, such as the eyes, eyebrows, nose, lips, and chin and their spatial relationships, or (ii) the overall (global) analysis of the face image that represents a face as a weighted combination of a number of canonical faces. While the verification performance of the face recognition systems that are commercially available is reasonable , they impose a number of restrictions on how the facial images are obtained, sometimes requiring a fixed and simple background or special illumination. These systems also have difficulty in recognizing a face from images captured from two drastically different views and under different illumination conditions. It is questionable whether the face itself, without any contextual information, is a sufficient basis for recognizing a person from a large number of identities with an extremely high level of confidence [29]. In order that a facial recognition system works well in practice, it should automatically (i) detect whether a face is present in the acquired image; (ii) locate the face if there is one; and (iii) recognize the face from a general viewpoint (i.e., from any pose).
Facial, hand, and hand vein infrared thermogram: The pattern of heat radiated by
human body is a characteristic of an individual and can be captured by an infrared camera in an unobtrusive way much like a regular (visible spectrum) photograph. The technology could be used for covert recognition. A thermogram-based system does not require contact and is non-invasive, but image acquisition is challenging in uncontrolled environments, where heat emanating surfaces (e.g., room heaters and vehicle exhaust pipes) are present in the vicinity of the body. A related technology using near infrared imaging is used to scan the back of a clenched fist to determine hand vein structure. Infrared sensors are prohibitively expensive which is a factor inhibiting wide spread use of the thermograms.
Fingerprint: Humans have used fingerprints for personal identification for many centuries and the matching accuracy using fingerprints has been shown to be very high. A fingerprint is the pattern of ridges and valleys on the surface of a fingertip, the formation of which is determined during the first seven months of fetal development. Fingerprints of identical twins are different and so are the prints on each finger of the same person. Today, a fingerprint scanner costs about US $20 when ordered in large quantities and the marginal cost of embedding a fingerprint-based biometric in a system (e.g., laptop computer) has become affordable in a large number of applications. The accuracy of the currently available fingerprint recognition systems is adequate for verification systems and small- to medium-scale identification systems involving a few hundred users. Multiple fingerprints of a person provide additional information to allow for large-scale recognition involving millions of identities. One problem with the current fingerprint recognition systems is that they require a large amount of computational resources, especially when operating in the identification mode. Finally, fingerprints of a small fraction of the population may be unsuitable for automatic identification because of genetic factors, aging, environmental, or occupational reasons (e.g., manual workers may have a large number of cuts and bruises on their fingerprints that keep changing).
Gait: Gait is the peculiar way one walks and is a complex spatio-temporal biometric. Gait is not supposed to be very distinctive, but is sufficiently discriminatory to allow verification in some low-security applications. Gait is a behavioral biometric and may not remain invariant, especially over a long period of time, due to fluctuations in body weight, major injuries involving joints or brain, or due to inebriety. Acquisition of gait is similar to acquiring a facial picture and, hence, may be an acceptable biometric. Since gait-based systems use the video-sequence footage of a walking person to measure several different movements of each articulate joint, it is input intensive and computationally expensive.
Hand and finger geometry: Hand geometry recognition systems are based on a number of measurements taken from the human hand, including its shape, size of palm, and lengths and widths of the fingers. Commercial hand geometry-based verification systems have been installed in hundreds of locations around the world. The technique is very simple, relatively easy to use, and inexpensive. Environmental factors such as dry weather or individual anomalies such as dry skin do not appear to have any negative effects on the verification accuracy of hand geometry-based systems. The geometry of the hand is not known to be very distinctive and hand geometry-based recognition systems cannot be scaled up for systems requiring identification of an individual from a large population. Further, hand geometry information may not be invariant during the growth period of children. In addition, an individual's jewelry (e.g., rings) or limitations in dexterity (e.g., from arthritis), may pose further challenges in extracting the correct hand geometry information. The physical size of a hand geometry-based system is large, and it cannot be embedded in certain devices like laptops. There are verification systems available that are based on measurements of only a few fingers (typically, index and middle) instead of the entire hand. These devices are smaller than those used for hand geometry, but still much larger than those used in some other biometrics (e.g., fingerprint, face, voice).
Iris: The iris is the annular region of the eye bounded by the pupil and the sclera (white of the eye) on either side. The visual texture of the iris is formed during fetal development and stabilizes during the first two years of life. The complex iris texture carries very distinctive information useful for personal recognition. The accuracy and speed of currently deployed iris-based recognition systems is promising and point to the feasibility of large-scale identification systems based on iris information. Each iris is distinctive and, like fingerprints, even the irises of identical twins are different. It is extremely difficult to surgically tamper the texture of the iris. Further, it is rather easy to detect artificial irises (e.g., designer contact lenses). Although, the early iris-based recognition systems required considerable user participation and were expensive, the newer systems have become more user-friendly and cost-effective.
Keystroke: It is hypothesized that each person types on a keyboard in a characteristic way. This behavioral biometric is not expected to be unique to each individual but it offers sufficient discriminatory information to permit identity verification. Keystroke dynamics is a behavioral biometric; for some individuals, one may expect to observe large variations in typical typing patterns. Further, the keystrokes of a person using a system could be monitored unobtrusively as that person is keying in information.
Odor: It is known that each object exudes an odor that is characteristic of its chemical composition and this could be used for distinguishing various objects. A whiff of air surrounding an object is blown over an array of chemical sensors, each sensitive to a certain group of (aromatic) compounds. A component of the odor emitted by a human (or any animal) body is distinctive to a particular individual. It is not clear if the invariance in the body odor could be detected despite deodorant smells, and varying chemical composition of the surrounding environment.
Palmprint: The palms of the human hands contain pattern of ridges and valleys much like the fingerprints. The area of the palm is much larger than the area of a finger and as a result, palmprints are expected to be even more distinctive than the fingerprints. Since palmprint scanners need to capture a large area, they are bulkier and more expensive than the fingerprint sensors. Human palms also contain additional distinctive features such as principal lines and wrinkles that can be captured even with a lower resolution scanner, which would be cheaper. Finally, when using a high resolution palmprint scanner, all the features of the palm such as hand geometry, ridge and valley features (e.g., minutiae and singular points such as deltas), principal lines, and wrinkles may be combined to build a highly accurate biometric system.
Retinal scan: The retinal vasculature is rich in structure and is supposed to be a characteristic of each individual and each eye. It is claimed to be the most secure biometric since it is not easy to change or replicate the retinal vasculature. The image acquisition requires a person to peep into an eye-piece and focus on a specific spot in the visual field so that a predetermined part of the retinal vasculature could be imaged. The image acquisition involves cooperation of the subject, entails contact with the eyepiece, and requires a conscious effort on the part of the user. All these factors adversely affect the public acceptability of retinal biometric. Retinal vasculature can reveal some medical conditions, e.g., hypertension, which is another factor deterring the public acceptance of retinal scan based biometrics.
Signature: The way a person signs her name is known to be a characteristic of that individual. Although signatures require contact with the writing instrument and an effort on the part of the user, they have been accepted in government, legal, and commercial transactions as a method of verification. Signatures are a behavioral biometric that change over a period of time and are influenced by physical and emotional conditions of the signatories. Signatures of some people vary substantially: even successive impressions of their signature are significantly different. Further, professional forgers may be able to reproduce signatures that fool the system.
Voice: Voice is a combination of physiological and behavioral biometrics. The features of an individual’s voice are based on the shape and size of the appendages (e.g., vocal tracts, mouth, nasal cavities, and lips) that are used in the synthesis of the sound. These physiological characteristics of human speech are invariant for an individual, but the behavioral part of the speech of a person changes over time due to age, medical conditions (such as common cold), emotional state, etc. Voice is also not very distinctive and may not be appropriate for large-scale identification. A text-dependent voice recognition system is based on the utterance of a fixed predetermined phrase. A text-independent voice recognition system recognizes the speaker independent of what she speaks. A text independent system is more difficult to design than a text-dependent system but offers more protection against fraud. A disadvantage of voice-based recognition is that speech features are sensitive to a number of factors such as background noise. Speaker recognition is most appropriate in phone-based applications but the voice signal over phone is typically degraded in quality by the microphone and the communication channel.
7. Biometric Application
The practical applications of biometric technologies are diverse and expanding, as new needs are identified. By and large, biometric applications fall into two main categories: law enforcement and civilian applications.
Law enforcement: The law enforcement community is perhaps the largest biometric user group. Police forces throughout the world use AFIS (Automated Fingerprint Identification System) technology to process criminal suspects, match finger images and bring guilty criminals to justice. Forensic applications such as corpse identification, criminal investigation, terrorist identification, parenthood determination, missing children, etc.
Commercial applications such as computer network login, electronic data security, ecommerce, Internet access, ATM, credit card, physical access control, cellular phone, PDA, medical records management, distance learning, etc.
Government applications such as national ID card, correctional facility, driver’s license, social security, welfare-disbursement, border control, passport control, etc.
Some examples of biometric applications are listed below.
Banking
Banks have been evaluating a range of biometric technologies for many years. Fraud and general breaches of security must be controlled if banks are to remain competitive in the financial services industry. Automated teller machines (ATMs) and transactions at the point of sale are particularly vulnerable to fraud and can be secured by biometrics. Other emerging markets include telephone banking and Internet banking, both of which demand the utmost security for bankers and customers alike.
Computer Access
Fraudulent access to computer systems affects private computer networks and the Internet in the same way: confidence is lost and the network is unable to perform at full capacity until the breach in security is patched. Biometric technologies are proving to be more than capable of securing computer networks. This market area has phenomenal potential, especially if the biometrics industry can migrate to large-scale Internet applications. As banking data, business intelligence, credit card numbers, medical information and other personal data becomes the target of attack, the opportunities for biometric vendors are rapidly escalating.
Electronic Benefits Transfer (EBT)
Benefits systems are particularly vulnerable to fraud. The battle against fraud has been waged by welfare departments across many U.S. states for years. A variety of technologies are being evaluated, although fingerprint scanning is particularly widespread. AFIS technology and one-to-one verification are used to ensure that the benefit claimant legitimately receives a benefit check. Another development that may revolutionize the payment of benefits is Electronic Benefits Transfer (EBT), which involves loading funds onto a plastic card. The card can then be used to purchase food and other essentials in shops fitted with special point-of-sale smart card readers. Biometrics are well-placed to capitalize on this phenomenal market opportunity and vendors are building on the strong relationship currently enjoyed with the benefits community.
Immigration
Terrorism, drug-running, illegal immigration and an increasing throughput of legitimate travelers is putting a strain on immigration authorities around the world. It is essential for these authorities to quickly and automatically process law-abiding travelers and identify the lawbreakers. Biometrics are being employed in a number of diverse applications to make this possible. The U.S. Immigration and Naturalization Service (INS) is a major user and evaluator of biometric technologies. Systems are currently in place throughout the U.S. to automate the flow of legitimate travelers and deter illegal immigrants. Biometrics are also gaining widespread acceptance in Australia, Bermuda, Germany, Malaysia, and Taiwan.
National Identity
Biometrics are beginning to assist governments as they record population growth, identify citizens, and prevent fraud occurring during local and national elections. Often this involves storing a biometric template on a card which, in turn, acts as a national identity document. Fingerprint scanning is particularly strong in this area and programs are already underway in Jamaica, Lebanon, the Philippines, and South Africa.
Physical Access
More and more organizations are using biometrics to secure the physical movement of people. Schools, nuclear power stations, military facilities, theme parks, hospitals, offices and supermarkets across the globe employ biometrics to minimize security threats. As security becomes more important for parents, employers, governments and other groups, biometrics will be seen as a more acceptable and therefore essential tool. The potential applications are endless. Biometrics could even be employed to protect our cars and homes.
Prisons
Prisons, as opposed to law enforcement, use biometrics not to catch criminals, but to make sure that they are securely detained. A surprising number of prisoners simply walk out of prison gates before they are officially released. A wide range of biometrics are now being employed worldwide to secure prison access, police detention areas, enforce home confinement orders, and regulate the movement of probationers and parolees.
Telecommunications
With the rapid growth of global communications, cellular telephones, dial inward system access (DISA), and a range of telecommunication services are under attack from fraudsters. Cellular companies are vulnerable to cloning (a new phone is created using stolen code numbers) and new subscription fraud (a phone is obtained using a false identity). Meanwhile, DISA — which allows authorized individuals to contact a central exchange and make free calls — is being targeted by telephone hackers. Once again, biometrics are being called upon to defend this onslaught. Speaker ID is well suited to the telephone environment and is making inroads into these markets.
Time & Attendance
Recording and monitoring the movement of employees as they arrive at work, take breaks, and leave for the day was traditionally performed by "clocking-in" machines. However, manual systems can be circumvented by someone "punching in" for someone else, a process known as "buddy punching." This disrupts time management and unit costing exercises and costs companies millions of dollars. Replacing the manual process with biometrics prevents abuses of the system. In addition, biometrics can be incorporated with time management software to produce management accounting and personnel reports.
8. Advantages and Disadvantages
In general the biometric systems have the following advantages.
- It is significantly more difficult to copy, share, and distribute biometrics with as much ease as passwords and tokens.
- Biometrics cannot be lost or forgotten and online biometrics-based recognition systems require the person to be recognized to be present at the point of recognition.
- It is difficult to forge biometrics and extremely unlikely for a user to repudiate, for example, having accessed a computer network.
- Further, all the users of the system have relatively equal security level and one account is no easier to break than any other (e.g., through social engineering methods).
- Biometrics introduces incredible convenience for the users (as users are no longer required to remember multiple, long and complex, frequently changing passwords) while maintaining a sufficiently high degree of security.
Merits and demerits of some biometric systems:
Retinal scans (electronic scan of the innermost layer of the eyeball's wall):
Advantages: Retina generally remains stable through life, ensuring accuracy. –
Disadvantages: Requires close physical contact MW scanning device; may not be generally accepted by public.
Iris recognition (recording of iris using standard video technology):
Advantages: Non-invasive procedure (close physical contact not required).
Disadvantages: Relatively expensive; requires large amount of computer storage; may not be generally accepted by public.
Finger imaging (recording of fingerprint using optical scanner):
Advantages: Widely accepted by public and law enforcement communities as reliable identification.
Disadvantages: Requires close physical contact with scanning device; residue on finger may cause recognition problems; has criminal overtones.
Hand geometry (three-dimensional recording of length, width and height of hand and fingers, using optical scanner):
Advantages: User-friendly; requires small amount of computer storage space.
Disadvantages: Isn't as unique as other biometric methods; hand injury can cause recognition problems.
Facial thermography or imaging (photograph of face converted into digital code):
Advantages: Non-invasive procedure.
Disadvantages: People who look alike can fool scanner; people can alter their appearance and facial hair can fool device.
Voice verification or recognition (acoustic signal of voice converted into digital code):
Advantages: Works well over the telephone.
Disadvantages: Requires large amount of computer storage; people's voices can change; background noises can interfere.
Signature recognition (computer record of pen/stylus speed, pressure, direction and other characteristics of signature):
Advantages: People are used to providing a signature.
Disadvantages: Poor long-term reliability; accuracy difficult to ensure.
9. Limitations of biometric systems
Biometric systems that operate using any single biometric characteristic have the following limitations:
1. Noise in sensed data: The sensed data might be noisy or distorted. A fingerprint with a scar, or a voice altered by cold are examples of noisy data. Noisy data could also be the result of defective or improperly maintained sensors (e.g., accumulation of dirt on a fingerprint sensor) or unfavorable ambient conditions (e.g., poor illumination of a user's face in a face recognition system). Noisy biometric data may be incorrectly matched with templates in the database (see Figure 5) resulting in a user being incorrectly rejected.
2. Intra-class variations: The biometric data acquired from an individual during authentication may be very different from the data that was used to generate the template during enrollment, thereby affecting the matching process. This variation is typically caused by a user who is incorrectly interacting with the sensor, or when sensor characteristics are modified (e.g., by changing sensors - the sensor interoperability problem) during the verification phase. As another example, the varying psychological makeup of an individual might result in vastly different behavioral traits at various time instances.
3. Distinctiveness: While a biometric trait is expected to vary significantly across individuals, there may be large inter-class similarities in the feature sets used to represent these traits. This limitation restricts the discriminability provided by the biometric trait. Golfarelli et al. have shown that the information content (number of distinguishable patterns) in two of the most commonly used representations of hand geometry and face are only of the order of 105 and 103, respectively. Thus, every biometric trait has some theoretical upper bound in terms of its discrimination capability.
4. Non-universality: While every user is expected to possess the biometric trait being acquired, in reality it is possible for a subset of the users to not possess a particular biometric. A fingerprint biometric system, for example, may be unable to extract features from the fingerprints of certain individuals, due to the poor quality of the ridges. Thus, there is a failure to enroll (FTE) rate associated with using a single biometric trait. It has been empirically estimated that as much as 4% of the population may have poor quality fingerprint ridges that are difficult to image with the currently available fingerprint sensors and result in FTE errors. den Os et al. report the FTE problem in a speaker recognition system.
5. Spoof attacks: An impostor may attempt to spoof the biometric trait of a legitimate enrolled user in order to circumvent the system. This type of attack is especially relevant when behavioral traits such as signature and voice are used. However, physical traits are also susceptible to spoof attacks. For example, it has been demonstrated that it is possible (although difficult and cumbersome and requires the help of a legitimate user) to construct artificial fingers/fingerprints in a reasonable amount of time to circumvent a fingerprint verification system.
10. Summary
Reliable personal recognition is critical to many business processes. Biometrics refers to automatic recognition of an individual based on her behavioral and/or physiological characteristics. The conventional knowledge-based and token-based methods do not really provide positive personal recognition because they rely on surrogate representations of the person’s identity (e.g., exclusive knowledge or possession). It is, thus, obvious that any system assuring reliable personal recognition must necessarily involve a biometric component. This is not, however, to state that biometrics alone can deliver reliable personal recognition component. In fact, a sound system design will often entail incorporation of many biometric and non-biometric components (building blocks) to provide reliable personal recognition. Biometric-based systems also have some limitations that may have adverse implications for the security of a system. While some of the limitations of biometrics can be overcome with the evolution of biometric technology and a careful system design, it is important to understand that foolproof personal recognition systems simply do not exist and perhaps, never will. Security is a risk management strategy that identifies controls, eliminates, or minimizes uncertain events that may adversely affect system resources and information assets. The security level of a system depends on the requirements (threat model) of an application and the cost-benefit analysis. In our opinion, properly implemented biometric systems are effective deterrents to perpetrators. There are a number of privacy concerns raised about the use of biometrics. A sound tradeoff between security and privacy may be necessary; collective accountability/acceptability standards can only be enforced through common legislation. Biometrics provides tools to enforce accountable logs of system transactions and to protect an individual’s right to privacy. As biometric technology matures, there will be an increasing interaction among the market, technology, and the applications. This interaction will be influenced by the added value of the technology, user acceptance, and the credibility of the service provider. It is too early to predict where and how biometric technology would evolve and get embedded in which applications. But it is certain that biometric-based recognition will have a profound influence on the way we conduct our daily business.
11. Glossary
The following is an alphabetical glossary of biometric and
biometric-related terms that appear in I/O Sofware's web site, and in the
biometrics industry in general.
Algorithm
A sequence of instructions that tell a biometric system how to solve a
particular problem. An algorithm will have a finite number of steps and is
typically used by the biometric engine to compute whether a biometric sample and
template are a match.
American National Standards Institute (ANSI)
Established in 1918, ANSI is a voluntary organization that creates standards for
the computer industry. The FBI commissioned ANSI to create an image standard for
the exchange of fingerprint data between AFIS systems.
Application Programming Interface (API)
A set of services or instructions used to standardize an application.
Attempt
The submission of a biometric sample to a biometric system for identification or
verification. A biometric system may allow more than one attempt to identify or
verify.
Authentication
The action of verifying information such as identity, ownership or
authorization. The preferred biometric term is verification.
Authentication Routine
A cryptographic process used to validate a user, card, terminal, or message
contents. Also known as a handshake, the routine uses important data to create a
code that can be verified in real time or batch mode. (see verification)
Automated Fingerprint Identification System (AFIS)
A specialized biometric system that compares a single finger image with a
database of finger images. In law enforcement, AFIS is used to collect
fingerprints from criminal suspects and crime scenes. In civilian life,
fingerprint scanners are used to identify employees, protect sensitive data,
etc.
Automatic ID/Auto ID
An umbrella term for any biometric system or other security technology that uses
automatic means to check identity. This applies to both one-to-one verification
and one-to-many identification.
Behavioral Biometric
A biometric that is characterized by a behavioral trait that is learned and
acquired over time, rather than a physical or physiological characteristic
(contrast with physical biometric).
Bifurcation
A branch made by more than one finger image ridge.
Binning
Taking advantage of different fingerprint pattern classifications to reduce the
number of comparisons that must be performed to find a match in an
identification system. Enrolled fingerprints that can be classified with a high
degree of confidence are assigned to "bins" corresponding to each
classification. A submitted print that cannot be classified with high confidence
must be matched against all the bins (the entire database), but prints that can
be classified need only be matched against the corresponding bin or bins.
Biometric
A measurable, physical characteristic or personal behavioral trait used to
recognize the identity, or verify the claimed identity, of an enrollee.
Biometric Application Programming Interface (BAPI)
See I/O Software's BAPI Glossary.
Biometric System
An automated system capable of capturing a biometric sample from an end user;
extracting biometric data from that sample; comparing the biometric data with
that contained in one or more reference templates; deciding how well they match;
and indicating whether or not an identification or verification of identity has
been achieved.
Biometrics
The automated technique of measuring a physical characteristic or personal trait
of an individual and comparing that characteristic to a comprehensive database
for purposes of identification.
Block Cipher
A symmetric cipher which encrypts a message by breaking it down into blocks and
encrypting each block.
BPI
Bits per inch, as on a magnetic stripe card.
CAPI
Cryptographic Application Programming Interface.
CSP
Cryptographic Service Provider.
Capture
The method of taking a biometric sample from the end user.
Cipher
An encryption/decryption algorithm.
Ciphertext
Encrypted data.
Classification
A scheme for categorizing fingerprints according to their overall patterns. Some
fingers do not fit into any of the classes, and some may have attributes of more
than one class. (see binning)
Coding
Image processing software for extracting minutiae features from the image.
Comparison
The process of comparing a biometric sample with a previously stored reference
template or templates. (see one-to-many and one-to-one)
Cryptography
The art and science of using mathematics to secure information and create a high
degree of trust in the electronic realm. (see public key and private key)
Cryptographic Key
(see key and public key)
Cryptosystem
An encryption/decryption algorithm (cipher), together with all possible
plaintexts, ciphertexts and keys.
Data Encryption Standard (DES)
Data Encryption Standard, a block cipher developed by IBM and the U.S.
Government in the 1970s as an official standard.
Decryption
The inverse (reverse) of encryption.
Demographic Data
Census information about an individual, such as name, address, gender, race, and
year of birth.
Digital Signature
The encryption of a message digest with a private key.
Direct Fingerprint Reader (DFR)
A device capable of scanning finger images directly from an individual's
fingers.
Electronic Benefits Transfer (EBT)
Electronic Benefits Transfer enables automatic benefits distribution. It is
currently implemented in WIC and Food Stamps programs.
Encryption
The transformation of plaintext into an apparently less readable form (called
ciphertext) through a mathematical process. The ciphertext may be read by anyone
who has the key that decrypts (undoes the encryption of) the ciphertext.
End User
A person who interacts with a biometric system to enroll or have his/her
identity checked.
Enrollee
A person who has a biometric reference template on file.
Enrollment
The process of collecting biometric samples from a person and the subsequent
preparation and storage of biometric reference templates representing that
person's identity.
Enrollment Time
The time a person must spend to have his/her biometric reference template
successfully created.
Enrollment Station
A workstation at which an individual's biometrics (fingerprint, voiceprint,
etc.) and personal information (name, address, etc.) can be entered into a
bioidentification system.
Extraction
The process of converting a captured biometric sample into biometric data so
that it can be compared to a reference template.
False Acceptance Rate (FAR)
The probability that a biometric system will incorrectly identify an individual
or will fail to reject an impostor. Also known as the Type II error rate.
False Rejection Rate (FRR)
The probability that a biometric system will fail to identify an enrollee, or
verify the legitimate claimed identity of an enrollee. Also known as the Type I
error rate.
Finger Image
(see image database)
Fingerprint Identification Unit (FIU)
A biometric system capable of capturing, storing and comparing fingerprint data
for the purposes of verifying an individual's identity.
Fingerprint Template
A description of all the detected minutiae in a fingerprint pattern. The
template contains each minutia's x/y coordinate, slope, and type, thus
summarizing the characteristics of the fingerprint for purposes of matching the
fingerprint against candidates.
Identification
A one-to-many comparison of an individual's submitted biometric sample against
the entire database of biometric reference templates to determine whether it
matches any of the templates and, if so, the identity of the enrollee whose
template was matched. The biometric system using the one-to-many approach is
seeking to find an identity within a database, rather than verify a claimed
identity. (contrast with verification)
Image Database
The database that contains all fingerprint templates in the system. The image
database can contain images of the fingerprints, as well as photograph and
signature images.
International Standards Organization (ISO)
The major international standards-setting organization for cards of all types.
Key
A string of bits used widely in cryptography, allowing people to encrypt and
decrypt data; a key can be used to perform other mathematical operations as
well. Given a cipher, a key determines the mapping of the plaintext to the
ciphertext. (see private key and public key)
Key Management
The various processes that deal with the creation, distribution, authentication,
and storage of keys.
Live Capture
The process of capturing a biometric sample by an interaction between an end
user and a biometric system.
Match/Matching
The process of comparing a biometric sample against a previously stored template
and scoring the level of similarity. An accept or reject decision is then based
upon whether this score exceeds the given threshold.
Minutiae
Points corresponding to the ridge endings, deltas, and bifurcations of a finger
pattern. Minutiae are described in a fingerprint template.
Minutiae Database
The database that contains all fingerprint templates in the system. The minutiae
database is contained within the image database.
Non-repudiation
A property of a cryptosystem. Non-repudiation cryptosystems are those in which
the users cannot deny actions they performed.
One-to-Many
Fingerprint search that compares the minutiae from a candidate fingerprint image
against the fingerprint minutiae database to determine whether or not the
candidate exists in the database. (synonym for identification.)
One-to-One
Fingerprint search that compares the minutiae from an individual's live
fingerprint image against fingerprint minutiae stored on a card or in a specific
database record to determine whether or not the individual is who he or she
claims to be. (synonym for verification.)
Original Equipment Manufacturer (OEM)
A biometric organization (manufacturer) that assembles a complete biometric
system from parts, or a biometric module for integration into a complete
biometric system.
Password Bank
A database for storing username, password and other personal information, to be
released upon verification of an individual's identity.
Personal Identification Number (PIN)
A security method whereby a (usually) four-digit number is entered by an
individual to gain access to a particular system or area.
Physical/Physiological Biometric
A biometric that is characterized by a physical characteristic rather than a
behavioral trait. (contrast with behavioral biometric)
Plaintext
The data to be encrypted.
Private Key
In public-key cryptography, this key is the secret key. It is primarily used for
decryption but is also used for encryption with digital signatures.
Public Key
In public-key cryptography, this key is made public to all. It is primarily used
for encryption but can be used for verifying signatures.
Public Key Cryptography
Cryptography based on methods involving a public key and a private key.
Public Key Infrastructure (PKI)
PKIs are designed to solve the key management problem. (see key management)
Password List (PWL)
(see password bank)
Recognition
The preferred term is identification.
Reference Template
Data that represents the biometric measurement of an enrollee used by a
biometric system for comparison against subsequently submitted biometric
samples.
Registration
Process of registering biometric data with a Fingerprint Identification Unit (FIU)
or other biometric system.
Rejection/False Rejection
When a biometric system fails to identify an enrollee or fails to verify the
legitimate claimed identity of an enrollee. Also known as a Type I error.
Response Time/Processing Time
The time period required by a biometric system to return a decision on
identification or verification of a biometric sample.
Smart Card
A card-shaped portable data carrier that contains one or more integrated
circuits for data storage and processing. A typical smart card chip includes a
microprocessor or CPU, ROM (for storing operating instructions), RAM (for
storing data during processing) and EPROM (or EEPROM) memory for nonvolatile
storage of information.
Software Developer's Kit (SDK)
A programming package that enables a programmer to develop applications for a
specific platform. Typically an SDK includes one or more APIs, programming
tools, and documentation.
Threshold
The acceptance or rejection of biometric data is dependent on the match score
falling above or below the threshold. The threshold is adjustable so that the
biometric system can be more or less strict, depending on the requirements of
any given biometric application.
Type I Error
The failure of a fingerprint identification system when it does not match a
candidate fingerprint pattern with its mating fingerprint pattern (in other
words, a failure to make a match that should have been made).
Type II Error
The failure of a fingerprint identification system when it matches a candidate
fingerprint pattern with a non-mating fingerprint pattern (in other words,
making a match that should not have been made).
Validation
The process of demonstrating that the system under consideration meets in all
respects the specification of that system.
Verification
A comparison of two sets of biometrics to determine if they are from the same
individual; or, in fraud prevention applications, a one-to-one comparison of a
live finger and a previously enrolled record to ensure that the applicant is who
he/she claims to be.
References
IEEE Transactions on Circuits and Systems for Video Technology, Special Issue on Image- and Video-Based Biometrics, Vol. 14, No. 1, January 2004.
Web resources
http://www.findbiometrics.com/