Computer Security
There are three main things that protect your computer from harmful viruses and hackers:
1. An anti-virus program - to protect against viruses and harmful code which can "infect" your computer and corrupt information and/or cause your computer to crash.
2. A firewall - A program or piece of hardware designed to prevent hackers from gaining access to your computer to either steal information, or to use your computer to hack other people. Firewalls also stop malicious programs called "Trojan horses" from letting hackers take control of your computer.
3. Common sense - A great deal of hackers and viruses could be stopped with just a little common sense. Knowing how viruses and hackers work is the only way to stop them from entering your computer.
Here are a number of anti-virus programs that I recommend:
1. Norton Antivirus - This is the anti-virus program that I personally use. The best feature is that it runs constantly in the background, thus protecting you against viruses on websites. The software is quite easy to use, and it caters for all levels of competency. Get a trial version of Norton Antivirus at: http://www.symantec.com/downloads.
2. McAfee Antivirus - I have never used this program, but I have heard from others that it is just as good as Norton. You can get a trial version at: http://software.mcafee.com/centers/download/default.asp.
3. Housecall - This is an online virus and Trojan checker. It is free, but I find it irritating because it is so slow. Apparently after the first scan it gets quicker though. Get your free virus scan at: http://housecall.antivirus.com/housecall/start_pcc.asp.
4. AVG - This free virus scanner/remover has received heaps of praise from all round. It is not quite as good as a full-blown anti-virus that you pay for, but it is the best free anti-virus that you will find.
Remember: An anti-virus program is only effective if you keep it up to date by downloading the latest virus definitions. An out of date virus program is almost as bad as no program at all!
And here are a number of firewalls I recommend:
1. Norton Firewall - This is the firewall that I use. It's fairly easy to set up and I haven't had any hassles with hackers or anybody. I think there is now a trial version available, or you can buy it from www.symantec.com.
2. Zone Alarm - This is a very popular free firewall. It was (as far as I know) the first firewall to pass GRC's Leak Test (http://grc.com/lt/leaktest.htm). You can download Zone Alarm at www.zonealarm.com. I might add that I have set up my Norton Firewall so that it also passes the leaktest. It is very easy, you just set your firewall to notify you each time a program accesses the Internet, and to give you the option of accepting or rejecting the connection.
Set it to not allow any programs to access the Internet without your permission. This can be a pain for the first couple of days, but it's a real reassurance once it's finished bugging you. It helps to immunize you against trojan horses too! I would strongly recommend paying for Zone Alarm Pro, because it has many features that make it substantially more secure than the free Zone Alarm.
Note: If you speak in Yahoo! chat in voice (and in any voice chat program), you may need to make a firewall rule to allow the voice chat, otherwise people might say that you are breaking up!
Here are a couple of tips and tricks to help you defend against viruses, Trojans and hackers:
Security:
1. Go and test how secure your system is at www.grc.com. There are a number of tests there to check if you have any security holes. You can also test your computer in a variety of ways at http://www.pcflank.com/. This test includes browser security, an exploits test and more. It can take quite a while though.
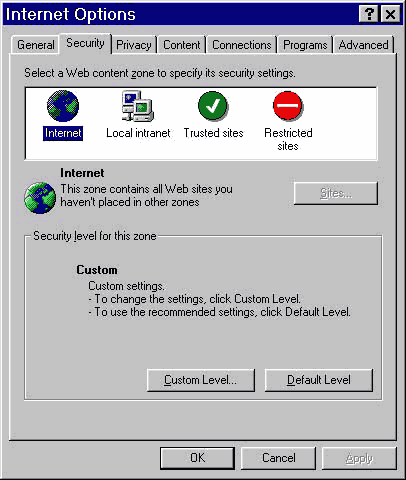
2. Adjust your browser security settings. If you are in Internet Explorer, go to Tools>Internet Options. Go to the Security tab, and ensure that you change the security settings for ALL of the domains (Internet, local intranet, trusted sites and restricted sites) mentioned in the little box. DO NOT make the "Restricted Sites" less restricted. That is one easy way to get a virus or other malicious material!

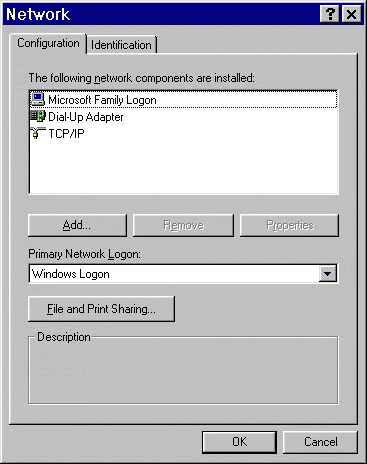
3. If you are not running a network, you may wish to delete the networking protocols. These can be easily retrieved if you ever wish to run a network. Go to Start>Settings>Control Panel and go to Network. I only have:
a) Microsoft Family Logon
b) Dial-up adapter
c) TCP/IP
You can delete the other protocols (56K users only). Also, set Primary Network Logon to Windows Logon. Now read my section on Disabling NetBIOS to complete the job!
If you are using cable modem, or some other equipment that requires other protocols, refer to your user's manual. I have a 56K dial-up modem and this configuration works just fine. It not only improves your security, but it speeds up your Internet too!!
4. Set your firewall so that it does not allow any programs to access the Internet without prompting you. By doing this, you can stop many trojan horses, e.g. Netbus from doing any harm, as the controller of the trojan can't communicate with it. That is really good! I also use this to prevent many programs from displaying adverts or downloading when I don't want them to. If your firewall has an option to create firewall rules for you, make sure you disable it, because it will ruin all your hard work. It can also prevent some programs from working properly.
Privacy:
1. Want to know just how much people can find out about you? You'd be VERY surprised. Pop in to www.privacy.net/analyze to check how much they can tell you about your PC and your browsing habits. They even tell you your screen resolution!!
2. Once you've done the privacy analysis, go to their home page www.privacy.net to find out how to make your browsing habits and computer specifications less accessible.
3. I'd definitely encourage turning off the auto-complete feature in Internet Explorer for certain things.
In Internet Explorer, go to tools>Internet options. Click on the "content" tab and click the "AutoComplete" button. Ensure that AutoComplete for "forms" and "user names and passwords on forms" is unchecked (i.e. there is no mark in the box next to them). Also click "Clear Forms" and "Clear Passwords", to delete any information that may already be on your computer. Click OK until you have closed all the windows.
The reason for these measures is so that if somebody gets into your computer, they can't get hold of personal information, passwords and credit card numbers. If you have a firewall, this is less likely to happen, but especially with credit card numbers and passwords I'd be very careful.
4. Make sure that you never give out your name, address, telephone number or any other private details to a person on the Internet, no matter how nice he/she appears to be. Just from a little crumb of information, they can find out everything about you, and some maniacs on the Internet could even start stalking you in real life!! This is something that you definitely don't need in your life. Remember, a person on the Internet can pretend to be whoever or whatever they wish, and you would never even know it! Stalkers on the Internet almost never appear suspicious or evil, just like most criminals in real life.
5. Similarly, be careful what information you give out in online surveys, feedback forms, and registering for a service or user name. If a service requires your address, telephone number or something private, unless it's a very reputable company like Yahoo!, never fill it in. Just work out whether it is more important to you to join, or have your privacy. Many companies sell your information to other companies, and then you wonder why you get spam e-mails, telemarketing phone calls, door-to-door advertisers etc!!
6. As boring as it may be, I recommend that you read the End User License Agreements (EULA) for all products you download/install and everything you sign up for on the Internet. Often these agreements can contain some startling clauses. You don't want to find yourself in trouble for not following the terms of the agreement!
1. Do not open e-mail attachments unless you are 100% sure that the person they were sent from would actually send you such a file. e.g., if you get a file from your mother telling you to check out these great pics of Anna Kournikova, you can probably be quite sure that all is not as it seems!
Remember: If in doubt as to whether the attachment is genuinely from the sender, just send them an e-mail to confirm.
2. Be careful of virus hoaxes that may be sent to you by e-mail. Visit www.kumite.com/myths to find out more about hoaxes and myths!
3. Viruses can also be transmitted through websites! Ensure that your virus scanner scans all files as they are written to the hard drive, because otherwise you can get infected from a malicious website!
4. Disable Windows Scripting Host (WSH). This may well be one of the most important tips on this page! Many, many viruses are run using the WSH. If you disable it, many viruses cannot run and can not damage your computer!! More than likely, you will never even need to use this "feature" in Windows. To disable the WSH, go to start>settings>control panel. Go to add/remove programs and click on the windows setup tab. Click on accessories and click details... at the bottom of the window. One of the last items on the list should be the WSH. To disable it, make sure that the box next to WSH in not checked (no tick in the box). Click OK until all the windows are closed. You will probably need to reboot your computer after you are finished saving all your work.
5. Show file extensions. Many viruses, especially those e-mailed, have double-extensions, like virus.txt.exe. This file is an exe file, not a txt file!! However, if you have Hide file extensions for known file types enabled, the file will show as virus.txt only! This can be very deceiving. To show all file extensions, go to My computer, click view, click folder options..., click on the view tab and make sure that that Hide file extensions for known file types does not have a check mark (tick) in it. If it does, uncheck (untick) it and press ok. Now you will be safe from this nasty virus method!
6. Common extensions for viruses include: exe, js, vbs, pif, com, bat.
1. ![]() You can
e-mail me and I'll try to set up a time to give your computer a fairly
comprehensive security scan for free. I have a number of programs that
can test for security issues and open ports etc. I would, naturally, provide
with advice on how to fix any security holes that do exist.
You can
e-mail me and I'll try to set up a time to give your computer a fairly
comprehensive security scan for free. I have a number of programs that
can test for security issues and open ports etc. I would, naturally, provide
with advice on how to fix any security holes that do exist.
2. Don't get into arguments with people (especially hackers!) in chat rooms. In many cases your IP address can be easily obtained and the person you are arguing with may decide to hack you! If you get into an argument with somebody you suspect may be a hacker, exit the room immediately and close all the chat windows and programs.
3. Do not visit hacking websites. Many of these contain ActiveX controls that can hack your computer through the website (even if you have a firewall) and can do other damage.
Remember: When you visit a website, your IP address is automatically recorded on the web server log. Visiting hacking websites can lead to you personally being the target of a group of hackers!
4. If you have reason to suspect that your are being hacked, e.g. you have lost control of your computer and somebody is moving around the mouse and opening programs, switch off your modem! Nobody can hack you once you have your modem off. If you have a dial-up modem, your IP address probably changes each time you dial up. This way, they can't hack you again unless they planted files on your computer to notify them when you're online and what your IP address is. This is unlikely however.
5. If you suspect that somebody is currently snooping:
Close down all your programs, press alt-ctrl-del once to close down all background programs except explorer, systray and your anti-virus and firewall. Go to start>run and type command. This brings up the MS-DOS prompt. Type in Netstat, and all connections to your computer will be revealed. If you are not on a network, and there is anything that shows up when you type netstat, then somebody is currently connected to your computer. Write down all the information that comes up on your screen, i.e. protocol, ip number, port etc, and then switch off your modem. Then e-mail me the details of the netstat report (from a different computer, or after dialling-up again if you have a dial-up), and I'll see what I can do :)
6. Get Trojan Remover by Simply Super Software. You can get the program from http://www.simplysup.com/tremover/. It is shareware, and must be registered after 30 days. This is not a big problem, however, because in that time you can remove all the trojans currently on your system. Unfortunately, you will not be protected from new ones after the 30 days.
When the program is installed, open it and click on the little ambulance icon on the toolbar, second icon from the left. This will check your computer for active trojans. When you're done with that, you can do a full system scan by clicking on the flashlight icon, third from the left. I must warn you that this can take a long time if you have many files on your system. My scan took just over 2½ hours!!
You have a choice to delete or rename a trojan, when it is found, and Trojan Remover provides data about the trojan. If you rename a trojan, it can no longer be run, so it is harmless. It will still take up space on your hard drive and remains a potential risk, however. The better option is to delete the trojan, but only do this if you are sure the file is not legitimate.
Many people are not aware of spyware, and that is one of the reasons it is so dangerous. The definition of spyware is software that works for advertising companies, collecting data to sell for money. That doesn't sound too bad, does it? Well, it is!
Spyware products are also called advertising trojans. Have you ever encountered spyware? Probably. Whenever you download a program like Kazaa, Bearshare, Limewire, GoZilla! or many other useful programs, you are downloading spyware. It may be noted that many (even most) file sharing software programs contain spyware. There are luckily "clean" alternatives to most popular spyware products, so you needn't worry too much about losing out if you dump the spyware. If you would like to know of a clean alternative to a spyware product you have, or if you suspect your product might be spyware, you can visit www.spychecker.com and search their extensive database.
It is useful to note that some spyware programs give you options to reject the spyware. I am not sure if they still install the spyware regardless, but it's worth trying. Some names of popular spyware are Bonzi Buddy, Cygate, Gator and WebHancer. Do not install these programs no matter how useful or cute they seem!
To find out if you are "infected" with spyware, download a program called AdAware. This program will search for and, if you wish, remove all spyware found in your computer. A computer I recently "disinfected" had 1700 pieces of spyware on the hard drive! The computer was part of a network, and after disinfecting 4 computers, I had totalled over 5000 pieces of spyware on these computers. They were noticeably faster after they were cleaned!
Do note that some programs like Kazaa won't work after the spyware has been removed, so make use of AdAware's "backup" feature to be able to restore any unwanted removals if necessary. The good news is that Kazaa Lite has been released (unofficially of course) minus the spyware, so that you can still enjoy Kazaa.
So how does this all work? The spyware companies pay the software companies money to include their spyware in their products (like Kazaa and Go!Zilla), and that is often how these "free" software programs make a profit and stay afloat.
Spyware resides in your registry and your hard drive and invades your privacy. The spyware tracks where you go on the Internet and what you do there. It then reports back to "head office" and sends them all the information it has gathered. Often this includes e-mail addresses and website addresses. They then use this information to send spam (unsolicited e-mail) and to work out what method of advertising would be most effective. If you are getting mysterious advertising e-mails where they call you by your name, then you have probably been hit by spyware!
This trick took me so long to work out, that I decided to dedicate an entire section on it. NetBIOS is a service that is used primarily for file and printer sharing in networks. If you run a network, do not read this section; you'll probably just mess things up. If you don't run a network, then this section will get you one step closer to having a hacker-proof computer. Before you do the following steps, make sure that you have completed this
First, to see what I am talking about, go to control panel and then to Network. Select TCP/IP and click Properties. Click OK when you get the pop-up message. Now go to the NetBIOS tab. You should see that it says "I want to enable NetBIOS over TCP/IP". Problem is, that in all probability that text and the check-box next to it are greyed out! If it's not greyed out, just untick it, press ok and jump to the next paragraph. Now, how on earth are you supposed to disable it if it's greyed out? Well, it took quite a bit of thinking, frankly, but I finally found the solution. Click on the Bindings tab, and you should see that "Microsoft Family Logon" is in the box and is ticked. Untick it and click OK at the bottom. If it tells you that you need your Windows CD, just press cancel because you don't.
Now you should be prompted to reboot your computer. Reboot and then everything is finished! If you open up Network again you will be prompted that "You network is not complete. Do you want to continue?". In true Microsoft fashion it doesn't make an iota of difference which button you press! You should notice now that Microsoft Family Logon is no longer listed. Also, if you go to TCP/IP>NetBIOS again, you'll notice that the box is unticked, and is no longer greyed out! OK your way out of there, and you're done!
So you may ask "Well, why don't you just delete the Microsoft Family Logon?". Truth is I tried that and I could no longer dial up to my ISP (Internet Service Provider). Don't ask why, that's just what happened. It disabled NetBIOS, but that's no help if you can't connect to Internet! As soon as I restored the Family Logon it worked again. My method is, in my opinion, the simplest solution.
If you're wondering what made me go insane trying to work this out when I have a firewall anyway, it's that I am trying to make my computer as secure as possible even without a firewall running. If somebody manages to bypass your firewall, you don't want your computer to be easy hunting ground. Paranoid, yes, but well worth the hassle. GRC now shows all my ports as "closed" when I turn off the firewall. Previously, my Port 139 (NetBIOS) showed open. That's what triggered this whole story.
I have been meaning to add this section for a long time, as I feel that cookies are an issue that is widely misconceived and often leads to a lot of misinterpretation and even paranoia.
Cookies, quite simply, are text files. People moaning about "receiving cookies in their inbox" (of their e-mail), having "cookies and other programs causing havoc" and all other accusations are talking nonsense. A cookie is a text file placed in your Temporary Internet Files folder in order to help a website to provide more customized service, or to make your use of the website easier.
For example, Yahoo. If you tell Yahoo, or any other similar website, to remember your username and password when you log in, it places a cookie on your machine so that next time you access the website it can log you in automatically. If you delete the cookie, it will not log you in automatically unless you respecify it again when you next log in manually.
Another example where cookies are frequently used is forums. On Dr Boot, and many other forums, cookies are used so that you can keep track of which topics you have read, and which you have not. If it were not for cookies, you would have to check every single topic to see whether or not you have previously read it. This would obviously waste a lot of time.
If you have specific preferences on a website, such as colours and designs of various items, cookies can also keep track of this so that it can "remember" your preferences when you next visit the website. Ever had a website say "Welcome back [name]"? This is an example of cookies at work.
Now, if all that I have said so far is true, why do people consider cookies to be dangerous privacy invaders? Well, cookies can keep track of your movements within that specific website and see what links you click on and what you do. It cannot see where else you have been and it cannot track you once you leave the site. The reason that many websites track your movements, is to see what items customers find more interesting. Websites can often tell which website (singular) you visited before you visited their website, but this is hardly anything to worry about (and it has nothing to do with cookies).
If you want to see a cookie for yourself, and if this helps to convince you that they really are quite harmless, navigate to c:\windows\temporary internet files and open up any one of the text files that you find in that folder. Windows will warn you that this may be unsafe, but it can't be, so just ignore it.
I hope you have a better idea of what cookies are now, and can now inform paranoid friends, family and neighbours that they will not be eaten up by a cookie monster!