Some
knowledge on SmartCards is necessary in order to fully
understand the essence of our assignment. In this chapter we
will describe what a SmartCard is and what we use it for.
What is a
SmartCard?
A SmartCard
is a little plastic card, much like the credit cards that are
currently (1998) used. A big difference between a credit card
and a SmartCard is that a credit card has a magnetic stripe
on the back, which is used for data-storage, where the
SmartCard uses a microchip, that has some storage-space as
well. Besides the storage-space, it also has a
microprocessor, which gives the card its name:
"SmartCard". It is not a dumb data-storage device,
the processor enables the card to protect the data that is
stored inside the chip by cryptographic computations and
grants users access to certain areas of the card.
At this
moment, there are different types of cards in use. In an
average purse, one can find cards like a telephone card, one
or two banking cards, an identity card, one card used for
shopping and another one used for fuelling. The amount of
different cards is not only unpractical, it is irritating as
well. That is why a lot of research is being put in the
combination of cards. These cards are known as
"Multi-application cards" or "Multi Function
Cards" (MFCs).
More and
more applications are being integrated into one single card,
instead of a different card for each application. In the near
future, SmartCards will probably be used to store medical
records, to serve as an electronic purse and to guarantee
someone's identity, all in one. This is not easy to do. It is
important that each application has its own protected space
on the card and that outsiders cannot access the (usually)
private information that is stored.
SmartCards
and security
SmartCards
can store passwords in a way that they cannot be read from
the outside. In general a SmartCard can protect its data
using one of the following methods:
- Enciphering/Deciphering
data via a cryptographic algorithm making reads and
writes key-dependent.
- Integrity
of data is guaranteed using a cryptogram
("Message Authentication Code" (MAC)).
- Card
Holder Verification.
- Generating
a challenge, combined with a key, for authentication.
This method is known as the "Challenge Response
Method".
The first
method allows reads and writes of certain data on the SCC,
using a certain key. Data can be read and written enciphered,
using a certain key, so that only the receiver can decipher
the data with the same key. The outside world is unable to
read and understand the enciphered data.
The second
protection method provides the integrity of the data. The
output of a read-command will consist of the data and a
Message Authentication Code (MAC) computed over this data
with a specified key. With this mechanism, the receiver can
check if the data has been tampered with. Computing a MAC
over modified data will result in a different value.
The third
way of protecting a card's private data is by asking the
outside world for a "Card Holder Verification"
(CHV). The CHV is also known as "Personal Identification
Number" (PIN), but does not necessarily has to be a
number. A CHV has a length of 8 bytes. If a four-digit number
is used, only the first 2 bytes are used. The SmartCard can
store two CHVs per application. One CHV should normally be
sufficient, but the second one can be used to unblock the
first CHV, for instance. By entering a correct CHV, the card
can give access to a certain area.
Access can
also be restricted by presenting a challenge (a random
number) to the outside world. The outside world now has to be
able to present a cryptogram to the card. This cryptogram is
the result of a computation over the challenge (the random
number), in combination with a secret key. If the outside
world can create a proper cryptogram, using the secret key
and the random number, the card knows that the outside world
possesses the right secret key, after which access will be
granted to certain areas on the card. The opposite can be
possible as well. If the outside world wants to know if a
card is genuine or not, the external world generates a
challenge and presents it to the card. The card now uses this
random number and a secret key stored inside the card to
create a cryptogram, which will be presented to the outside
world.
SmartCard
internals
In this
section we will first compare the storage space of a
SmartCard to a floppy-disk after which we will compare the
chip on the card to a little computer. This comparison is
made, because the concepts of a floppy disk and a computer
are already known to most people.
SmartCard
architecture
Just like a floppy-disk, a SmartCard
has a directory-structure. Each SmartCard has a masterfile
(MF), containing pointers to the rest of the information
stored on the card. In the analogy of a floppy-disk, we would
call the masterfile the "root" of the floppy.
Furthermore there are dedicated files (DF) which can be
compared to directories and there are elementary files (EF)
which can be compared to the "normal" files on a
floppy-disk. This structure can be seen easily in the next
figure: 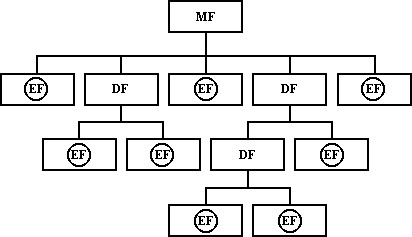
The directory structure of a Student ChipCard
So, a
SmartCard has a:
The
SmartCard processor
As said
before, the processor on the SmartCard can be seen as a
little computer. A SmartCard has the following components
([SCSol]) as can be seen in the next figure:
- a
Central Processing Unit (CPU)
- a Read
Only Memory (ROM)
- a
non-volatile read/write memory (EEPROM)
- a
temporary working memory (RAM)
- optionally
a crypto coprocessor
The SmartCard has control over the
access to application data by using a secure operating
system, safely stored in the ROM. 
Layout of a Secure Single Chip
The safety
of a SmartCard
SmartCards
are said to be very safe and protected against unauthorised
access, but this is not true. It is possible to attack a card
physically (a tamper) and it is possible to read private data
from the card, without even attacking it. The attacks are not
part of our subject but they are needed for an understanding
of the safety of SmartCards in general and in particular in
comparison with software only solutions.
We will
explain a bit more on the physical attacks possible to break
a SmartCard ([Anderson]). Although it is hard to physically
attack a SmartCard, it is possible. There have been attacks
that show that it is possible to remove the chip from a card
and to get rid of the epoxy layer on top of it, without
damaging the chip itself. After that, there are attacks
possible like changing the voltage, the temperature etc. It
is possible that after such attacks, the card will release
the security-bit. Some devices with an on-chip EEPROM will
release the lock-bit when UV light is focussed on the
security lock cell, which is located sufficiently far from
the rest of the memory. These simple attacks will not work on
the newer cards, but the protection of the newer cards is not
much better.
In 1995, a
description was given how to break a single-DES key, with a
key space of 64 bits, in 35 hours, using a brute-force
attack. A machine that would be able to do this would have
costed 1 million dollars at that time. However, the current
SmartCards have the ability of performing triple-DES
cryptographic computations with a double length key.
Therefore, breaking a triple-DES key succesfully is less
likely feasible. For the StudentSmartCard this method is not
very effective, because you only gain access to one card with
this method.
So,
SmartCards are relatively safe. What is possible, however, is
to read a lot of data from the card. After each transaction,
a log file is kept on the card. For instance, with a
home-made card-reader (details described at the homepage of
"Hacking In Progress (HIP)" [HIP]) it is easy to
read this log, containing the following information:
- the
kind of transaction
- a
status code
- remaining
amount after the transaction
- amount
of the transaction
- currency
- number
of the machine on which the transaction took place
- the
transaction number at that machine
- the
total amount this machine has processed so called
encrypted by adding two digits randomly to the
amount. Reading a different amount from the same
machine (i.e. a second transaction) will probably
already reveal the actual number
- date
and time (accuracy of 12 minutes)
Although the
national banks say that private information cannot be read,
the above shows the opposite.
The
Chipper, the ChipKnip and the GSM-card
The Chipper
and the ChipKnip are the current (1998) electronic purse
systems used in the Netherlands. At this moment, these cards
are not yet integrated. The main reason is that the cards are
not compatible. It is not possible to use the Chipper to pay
in shops, where the ChipKnip cannot be used in telephone
cells etc.
The Chipper
is the SmartCard of the Postbank and the ING. It is developed
by the Postbank and KPN-Nederland and is a true example of a
multi-function SmartCard system. It offers a "Service
Box" that contains a number of service slots which are
available for specific applications such as parking, loyalty
schemes or transport ([Chipper]). Card holders can safely add
up to ten different applications on the chip. Currently, the
Chipper can be used in telephone cells (with additional
memory space for telephone numbers) and busses. Payment
methods will be available for parking. The Chipper is
currently used in the Netherlands and in Australia.
The ChipKnip
is the SmartCard of the other Dutch banks, and is a copy of
the Proton (a SmartCard used in over 10 countries). The
ChipKnip is better integrated for payment in shops.
The GSM-SIM
card is the card used in GSM-telephones (digital cellular
phones). The SmartCard used in the GSM is called the SIM
(Subscriber Identification Module). This SIM is capable of
functions like storing abbreviated telephone numbers, storing
of short messages, etc. In April 1998, the code of the GSM
was cracked, which took about six hours. Still, it is easier
to circumvent analogue cells than digital cells, but it is a
nice example of a bad design.
The future
of SmartCards
In the
future, SmartCards will play an important role in the
authentication of individuals. All kinds of information will
be stored on these kinds of cards. The cards will become
MultiFunction Cards (MFCs) which means that multiple
applications will use the same card for various goals. For
example: medical records in combination with electronic purse
applications and identification information will be stored on
the same card. Practically anyone will be in possession of a
SmartCard. There are currently approximately 10 million
DES-cards in the Netherlands, used by the Dutch banks as
electronic purse. A smaller amount, but more important for us
is the number of students with a SCC (a total of 150.000).
The question is where the DES-SmartCards fit, since the
crypto-world seems to be heading for asymmetric cryptography
and RSA-SmartCards ([JanEnRoy]).



