Security issues in the news -
9/4/09
Here are some interesting graphs.
What are the most dangerous applications on your computer. (Dangerous in that they have been exploited in drive-by web infections.)
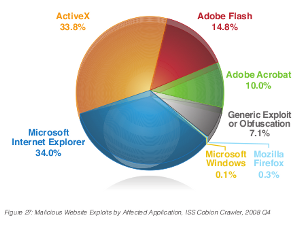
IBM
Infected web sites up almost 200%.
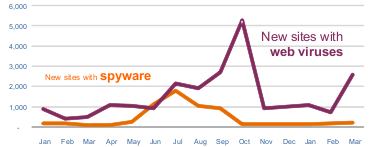
Message Labs
Firefox is a target for web-based exploits, if a small one (0.3%- see above), thanks to prompt security patches. But how quickly do users apply those patches? (Opera too.)
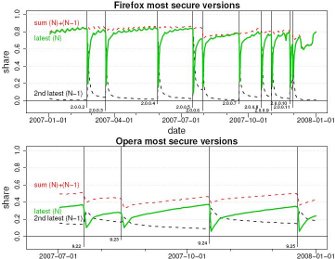
Firefox (In)Security Update Dynamics Exposed TechZoom
The usual advice applies- keep all web-facing applications up to date. The Secunia PSI vulnerability scanner will help you do this.
3/1/09
Let's start the new year with a review of the old from the BBC. To quote: "If 2007 was witness to the rise of the professional hi-tech criminal, then 2008 was the year they got down to work."
The report continues:
The poor detection of new malware by anti-virus products was confirmed in a report which claimed the rate could be as low as 40%. The report also highlights how this new malware is increasing installed by "code-injection" attacks on mainstream sites- drive-by downloads on hacked sites.
With this in mind, it's important to keep all web-facing applications up to date. Fully patched software is not vulnerable to exploits (with the rare exception of "zero-day" exploits- see below). A Secunia Blog report suggests most Windows users are not fully patched.
All the major browsers have patched security vulnerablities recently, so it's vital to ensure you have the latest version. Internet Explorer was subject to a "zero-day" exploit, with "in-the-wild" malware taking advantage of an un-patched security vulnerability- meaning IE users could get infected even running the latest version. IE7 seemed to be having a better time that IE6, which was subject to quite a few of these zero-day exploits, but the latest scare again raises doubts about the integration of IE into the operating system (especially in pre-Vista OS's) and the security (or not) of ActiveX. (Microsofts patch for this exploit required a reboot- a sure sign that the problem extended into the OS and was not just a browser issue- and the mitigating advice issued was to disable ActiveX and scripts in IE.)
I would personally advise using an alternative browser like Firefox and Opera, especially in Windows XP.
Firefox and Opera have a better security record than IE, but Firefox at least has also been the target of spyware. This happened again recently, but the story got distorted by some rather biased tellers. Reading some reports, you might have got the impression that the spyware installed via a Firefox exploit on a malicious web site- wrong. This was Firefox spyware installed by a Trojan horse. No Firefox exploit. And you had to run a malicious .exe file, not just visit a malicious site. (The spyware, by the way, hijacks Google searches.) The Firefox spyware is a malicious add-on, which produces a "new add-on has been installed" message- this also was a source of confusion, as the same message can also be shown when previously disabled add-ons are updated and re-enabled.
To avoid Firefox spyware, take the normal precautions for avoiding all malware- don't open email attachments or run downloaded exectable files unless you're really sure they're safe, and keep all web-facing software up-to-date. Even though this was not the issue here- Firefox add-ons can be malicious- do not install add-ons from untrusted sites.
*As pointed out above, the title of the thread is misleading, as the Spyware actually arrives via a Trojan horse, not a Firefox update.
Security News from 2008
Security News from 2007
What are the most dangerous applications on your computer. (Dangerous in that they have been exploited in drive-by web infections.)

IBM
Infected web sites up almost 200%.
Malicious websites – 2,797 new
sites blocked per day (an increase of 197.2% since February); Increased
threat from
web-borne malware.
web-borne malware.

Message Labs
Firefox is a target for web-based exploits, if a small one (0.3%- see above), thanks to prompt security patches. But how quickly do users apply those patches? (Opera too.)

Firefox (In)Security Update Dynamics Exposed TechZoom
The usual advice applies- keep all web-facing applications up to date. The Secunia PSI vulnerability scanner will help you do this.
3/1/09
Let's start the new year with a review of the old from the BBC. To quote: "If 2007 was witness to the rise of the professional hi-tech criminal, then 2008 was the year they got down to work."
Statistics gathered by firms
combating the rising tide of computer
crime reveal just how busy professional cyber thieves have been over
the last twelve months.
Sophos said it was now seeing more than 20,000 new malicious programs every day. 2008 was also the year in which Symantec revealed that its anti-virus software now protected against more than one million viruses.
The vast majority of these malicious programs are aimed at Windows PCs. Viruses made their debut more than 20 years ago but the vast majority of that million plus total have been created in the last two-three years.
Criminal gangs generate so many viruses for two main reasons. Firstly, many variants of essentially the same malicious program can cause problems for anti-virus software which can only reliably defend against threats it is aware of.
Sophos said it was now seeing more than 20,000 new malicious programs every day. 2008 was also the year in which Symantec revealed that its anti-virus software now protected against more than one million viruses.
The vast majority of these malicious programs are aimed at Windows PCs. Viruses made their debut more than 20 years ago but the vast majority of that million plus total have been created in the last two-three years.
Criminal gangs generate so many viruses for two main reasons. Firstly, many variants of essentially the same malicious program can cause problems for anti-virus software which can only reliably defend against threats it is aware of.
The report continues:
Before 2008 the preferred method
of attack was a booby-trapped attachment circulating by e-mail.
Provocative, pornographic and personal subject lines were used to trick people into opening the attachment. Anyone doing so risked having hi-tech criminals hijack their home computer and turn them to their own nefarious ends.
In 2008, said Graham Cluley from Sophos, the main attack vector started to shift. Increasingly, he said, attackers have tried to subvert webpages by injecting malicious code into them that will compromise the computer of anyone that visits.
By the close of 2008, said Mr Cluley, Sophos was discovering a newly infected webpage roughly every 4 seconds.
The type of page being booby-trapped had also changed, he said. Prior to 2008 gambling, pornographic and pirated software sites were much more likely to be unwitting hosts for the malicious code used to hijack visitors' machines.
In 2008 the criminals turned their attention to mainstream sites that had very large audiences and were vulnerable to the code-injection attack.
Provocative, pornographic and personal subject lines were used to trick people into opening the attachment. Anyone doing so risked having hi-tech criminals hijack their home computer and turn them to their own nefarious ends.
In 2008, said Graham Cluley from Sophos, the main attack vector started to shift. Increasingly, he said, attackers have tried to subvert webpages by injecting malicious code into them that will compromise the computer of anyone that visits.
By the close of 2008, said Mr Cluley, Sophos was discovering a newly infected webpage roughly every 4 seconds.
The type of page being booby-trapped had also changed, he said. Prior to 2008 gambling, pornographic and pirated software sites were much more likely to be unwitting hosts for the malicious code used to hijack visitors' machines.
In 2008 the criminals turned their attention to mainstream sites that had very large audiences and were vulnerable to the code-injection attack.
The poor detection of new malware by anti-virus products was confirmed in a report which claimed the rate could be as low as 40%. The report also highlights how this new malware is increasing installed by "code-injection" attacks on mainstream sites- drive-by downloads on hacked sites.

The typical scenario for a
web-driven bot is that you accidentally brush up against a compromised
website that has had an inserted which brings you (possibly via a chain
of other sites) into contact with an exploit server which delivers you
some malicious javascript (usually) that exploits your browser to take
control of the machine.
With this in mind, it's important to keep all web-facing applications up to date. Fully patched software is not vulnerable to exploits (with the rare exception of "zero-day" exploits- see below). A Secunia Blog report suggests most Windows users are not fully patched.
All the major browsers have patched security vulnerablities recently, so it's vital to ensure you have the latest version. Internet Explorer was subject to a "zero-day" exploit, with "in-the-wild" malware taking advantage of an un-patched security vulnerability- meaning IE users could get infected even running the latest version. IE7 seemed to be having a better time that IE6, which was subject to quite a few of these zero-day exploits, but the latest scare again raises doubts about the integration of IE into the operating system (especially in pre-Vista OS's) and the security (or not) of ActiveX. (Microsofts patch for this exploit required a reboot- a sure sign that the problem extended into the OS and was not just a browser issue- and the mitigating advice issued was to disable ActiveX and scripts in IE.)
I would personally advise using an alternative browser like Firefox and Opera, especially in Windows XP.
Microsoft: Big Security Hole in
All IE Versions SecurityFix
‘Extremely severe’ vulnerabilities in Opera browser ZDNet
Firefox joins security patch day treadmill ZDNet
‘Extremely severe’ vulnerabilities in Opera browser ZDNet
Firefox joins security patch day treadmill ZDNet
Firefox and Opera have a better security record than IE, but Firefox at least has also been the target of spyware. This happened again recently, but the story got distorted by some rather biased tellers. Reading some reports, you might have got the impression that the spyware installed via a Firefox exploit on a malicious web site- wrong. This was Firefox spyware installed by a Trojan horse. No Firefox exploit. And you had to run a malicious .exe file, not just visit a malicious site. (The spyware, by the way, hijacks Google searches.) The Firefox spyware is a malicious add-on, which produces a "new add-on has been installed" message- this also was a source of confusion, as the same message can also be shown when previously disabled add-ons are updated and re-enabled.
To avoid Firefox spyware, take the normal precautions for avoiding all malware- don't open email attachments or run downloaded exectable files unless you're really sure they're safe, and keep all web-facing software up-to-date. Even though this was not the issue here- Firefox add-ons can be malicious- do not install add-ons from untrusted sites.
*As pointed out above, the title of the thread is misleading, as the Spyware actually arrives via a Trojan horse, not a Firefox update.
Security News from 2008
Security News from 2007

