Web sites and servers can also be blocked completely using a feature of Windows called the hosts file.
Internet Explorer Restricted Zone
Be aware: web sites may try to trick you into downloading programs, or even try to do it without your knowledge! You are protected if a site is in your restricted zone. You could add sites one by one, but as there are thousands of 'bad' sites this would take a long time. Or you cold use Eric L. Howes' excellent:-
Restricted Sites List for Internet Explorer: IE-Spyad
"IE-SPYAD adds a long list of sites and domains associated with known advertisers, marketers, and crapware pushers to the Restricted sites zone of Internet Explorer. Once you merge this list of sites and domains into the Registry, the web sites for these companies will not be able to use cookies, ActiveX controls, Java applets, or scripting to compromise your privacy or your PC while you surf the Net. Nor will they be able to use your browser to push unwanted pop-ups, cookies, or auto-installing programs on your PC."
Download IE-Spyad.exe or IE-Spyad.zip (the first is self extracting and the latter you will have to unzip.) You will find a folder with a registry file which will add a list of sites to you browsers restricted sites list. Open the readme file for further instruction. (3 below.)
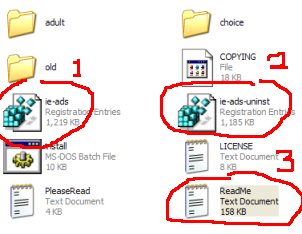
Open the IE-Spyad folder and click on the ie-ads registry file (1.) When updating after downloading a new folder, click on the ie-ads-uninst file (2) then click on the ie-ads registry file (1.)
Remember to check for updates regularly.
Once you have added sites to the restricted zone, you may notice warnings popping up while browsing concerning ActiveX or downloading files. These are because the site you are visiting is in the restricted zone, or contains material downloaded from a site in the restricted zone. For full information, see the comprehensive readme file which comes with IE-Spyad.
Finding IE Explorer Internet Zones
Internet Explorer > Properties > Security
1. Right click on the IE Explorer icon and select 'Properties'.
2. Select the Security tab.
3. Make sure the security level is set to high for restricted sites.
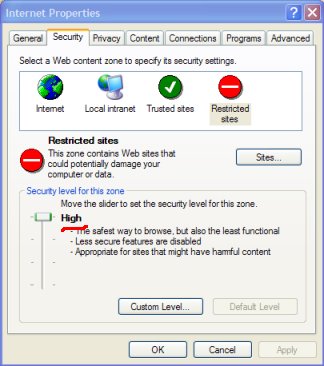
Click on 'Sites' to see all those bad sites IE-Spyad has added.
The hosts file: blocking web addresses
An internet address like anysite.com is only the human name for the site: a computer has to go off and find the computer address (IP address) for the site, which is four numbers separated by dots. It does this by looking it up on a database on the internet. However, before it does this, it looks in a local file called the hosts file, which can contain IP addresses for URLs.
The hosts file can be used to block spyware: enter the name of a web site that you want to block into the hosts file followed by the IP address of the local computer and any attempt to contact that site will be diverted, effectively up a blind alley, because the site isn't on your computer, and nothing will be displayed.
Blocking Unwanted Parasites with a Hosts File mvps.org
There is a facility in Spybot Search & Destroy to add a list of spyware servers to the hosts file if you start the program in advanced mode and go to tools.
It is also possible to block advertising servers in this way:
HOSTS File: Wholesale Blocking castlecops.com
The only problem with this method is that you don't know what has been blocked: looping back to the local computer in this way produces just a blank space. A neat way to receive a visual notification of what has happened is to use eDexter. This program will show an image when a page or part of a page is blocked in this way. I use this image while using the program:

This image shows why a page or part of a page has not appeared when using a block list in the host file and eDexter.
Spyware may try to add entries to the hosts file which misdirect an URL you type to a false address. For example, you may type mybank.com but be directed to a fake bank site by the hosts file. So, it's important to make sure the hosts file is not altered. One way of doing this is to use Winpatrol, which can lock the hosts file.